As a Windows or any other OS user, you should know about incoming and outgoing connections on your system. Knowing it is beneficial in the fight against malicious software. Your system requires “Open Ports” to create connections with the rest of the world over the Internet and using these ports, the hackers can infect your system. To find the “Open Ports” and other network information in Windows, you must use the “netstat” command.
The “netstat” or “Network Statistics” is a built-in Windows command-line utility that is also available on macOS and Linux distros. It allows you to view the network stats, the TCP/UDP endpoints, the interface, and routing information.
Master the “netstat” command in Windows by following this detailed guide.
How to Use the netstat Command in Windows
To use the netstat command on Windows, execute it with the following syntax:
netstat [-a] [-b] [-e] [-f] [-i] [-n] [-o] [-p proto] [-r] [-s] [-t] [-x] [-y] [interval]Where “[-a]” to “[interval]” are all options/flags of the “netstat” command that are used for different purposes. You can run the “netstat /?” command from CMD to get the details of each option:
netstat /?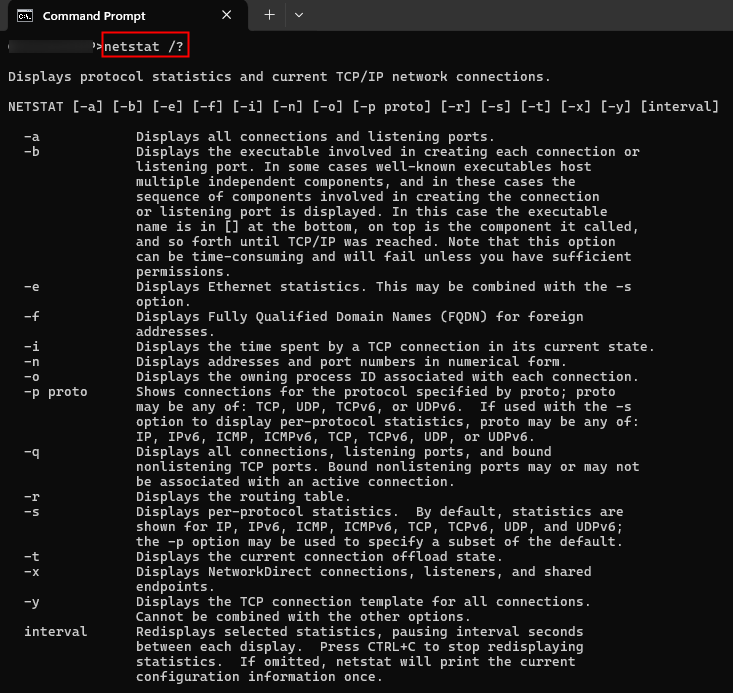
Let’s understand each of the above options via the following examples:
Example 1: Show All Connections | netstat -a Command Windows
The “-a” flag of the netstat command in Windows lets you view all listening ports and connections that include both active and inactive. Use it when you want a complete picture of your system’s network activity:
netstat -a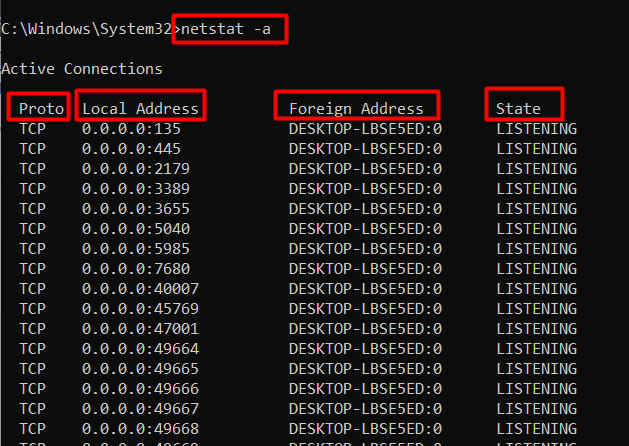
In the above output,
- The “Proto” stands for the “Protocol” and shows the name of the protocol currently in use.
- The “Local Address” shows the local IP address of the system along with the port in use.
- The “Foreign Address” specifies the remote system’s IP address to which your system is connected.
- The “State” shows the current status of the specified connection.
Example 2: Show Connections With Respective Processes | netstat -b Command Windows
If you want to view the applications or processes that are using the specified port, use the “-b” flag of the netstat as follows:
netstat -b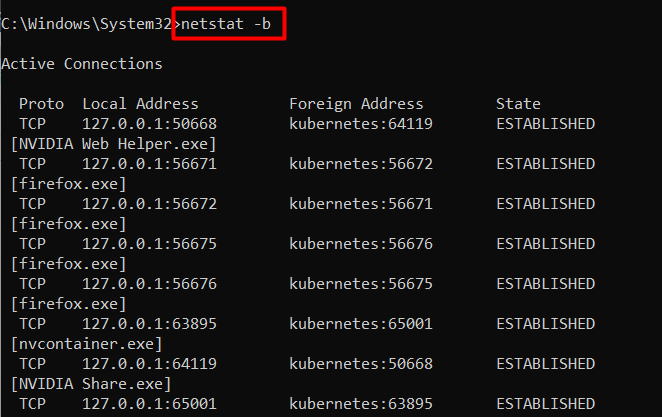
Note: Using the “netstat -b” command requires elevated (administrative) privileges.
Example 3: View Port Consumption Against Each Protocol | netstat -c Command Windows
To find the number of ports being used by each protocol against a specific program, use the “-c” flag of the netstat command as follows:
netstat -c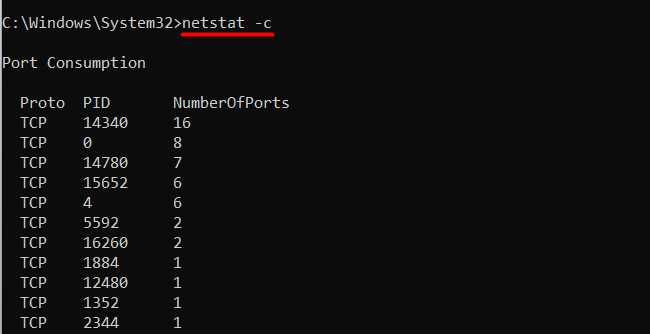
Example 4: View DSCP Values Against Each Protocol | netstat -d Command Windows
The “DSCP” value is how the system manages the network traffic and classifies the data packets. To view the “DSCP” value against each connection, use the “-d” flag as follows:
netstat -d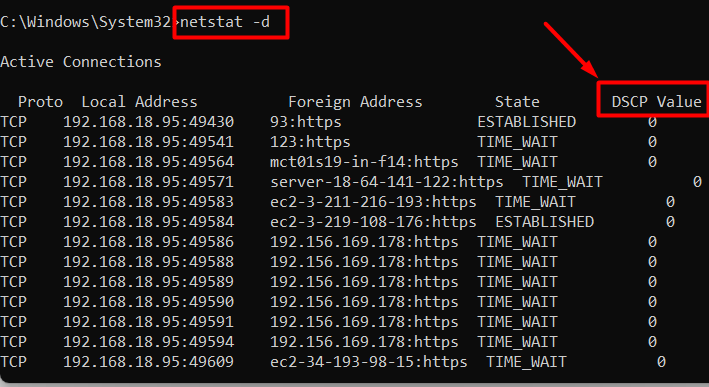
Get More Information about the DSCP Values using this link.
Example 5: View Ethernet/Interface Statistics | netstat Command Windows
The “Ethernet/Interface” statistics are the number of bytes and packets sent or received. To view these extended statistics, use the “-e” flag of the netstat command, as seen below:
netstat -e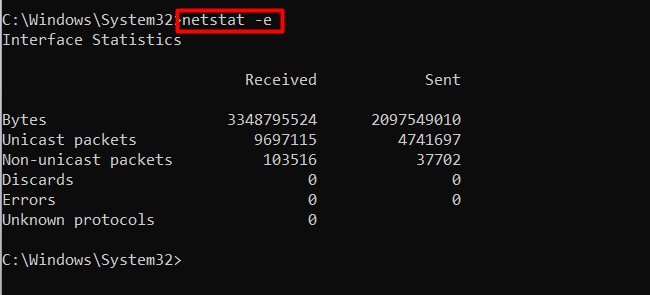
Example 6: View Fully Qualified Domain Names | netstat -f Command Windows
The “Fully Qualified Domain Names” or “FQDN” is the complete name of a computer system, a network, or a host. To view the “FQDN” associated with each protocol and port, use the “-f” flag of the netstat as follows:
netstat -f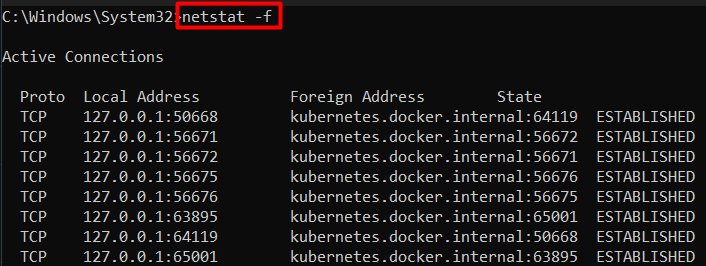
Example 7: View the Time Spent by TCP Connection | netstat -i Command Windows
You can execute the netstat command to get output with the time spent by the TCP connections in the current state. To do that, use the “-i” flag of the netstat command in Windows:
netstat -i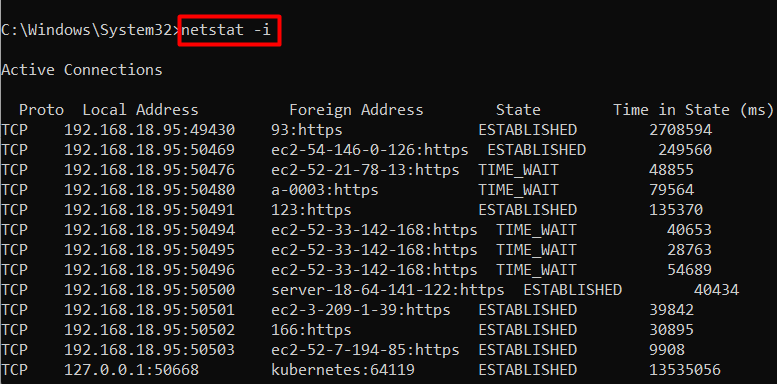
Example 8: View Port and IP Addresses in Numerical Form | netstat -n Command Windows
To customize the netstat command’s output and view the port number along with the IP address in numerical form, use the “-n” flag. It can be quicker and easier to read for large outputs:
netstat -n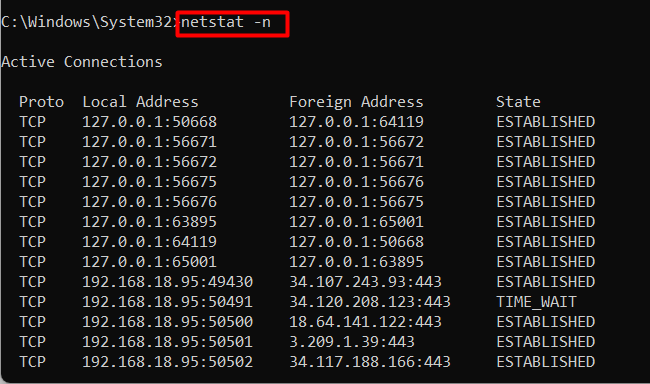
Example 9: View PID of Each Connection | netstat -o Command Windows
To find the PID associated with each connection on your system, use the “-o” flag of the netstat command. It is useful for advanced troubleshooting and security analysis because using it, you can identify suspicious programs using the specific port:
netstat -o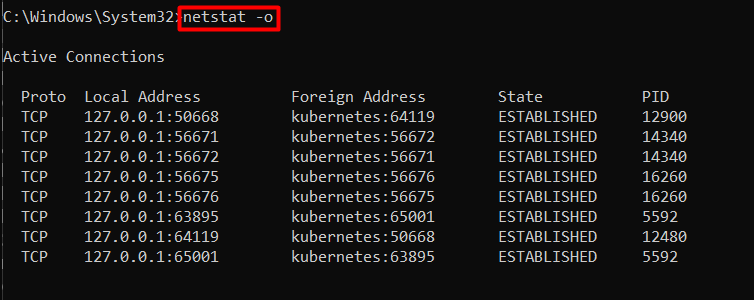
Example 10: View PID of Each Connection | netstat -p TCP Command Windows
You can use the netstat command to focus on a specific protocol. It can help isolate issues related to specific protocols. The “-p” flag followed by the “Protocol Name” is its format. The following command gives a detailed analysis of the “TCP”:
netstat -p TCP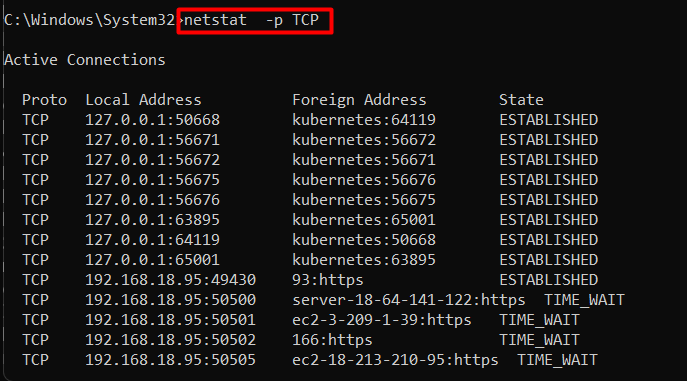
Example 11: View All Connections | netstat -q Command Windows
To view all connections, listening ports, and details associated with the active connection, use the “-q” flag of the netstat command. It can help you identify open ports and potential security risks:
netstat -q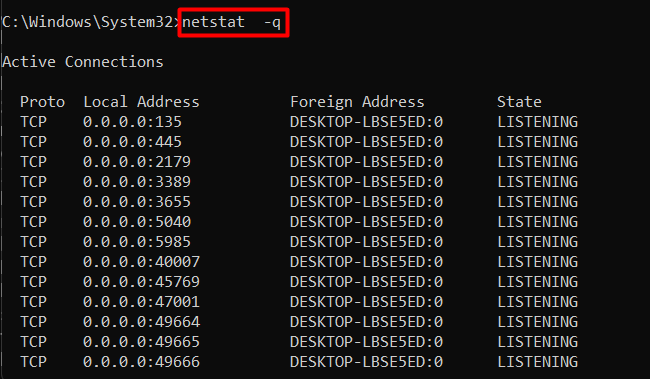
Example 12: View Routing Table | netstat -r Command Windows
The “-r” flag of the netstat command shows the routing table providing the details of how your system routes network traffic to different destinations. To view the routing table and interface list on Windows, use the following command:
netstat -r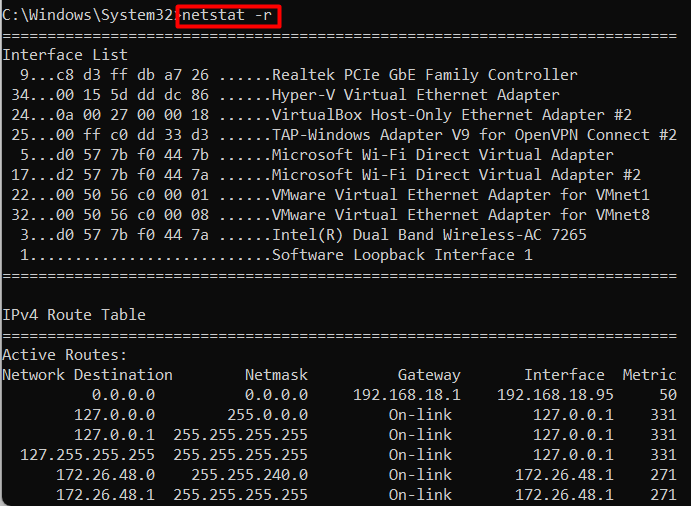
Example 13: View Detailed Statistics of All Protocols| netstat -s Command Windows
To get detailed statistics of all protocols, the “-s” flag of the netstat comes to the rescue. It could be useful for analyzing overall network traffic patterns:
netstat -s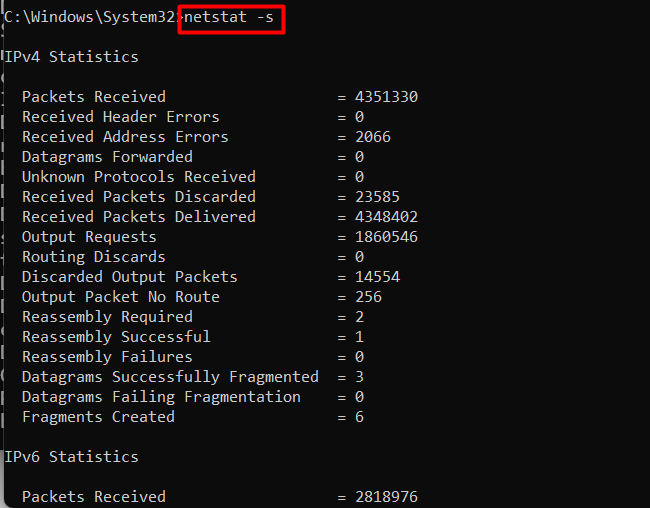
Example 14: View Offload State | netstat -t Command Windows
The “Offload State”, also called the “TCP Chimney Offload” is a feature for TCP connections that transfers the network load from the processor to the network device during the data transmission. To check if the “Offload State” is enabled on your system, use the following command:
netstat -t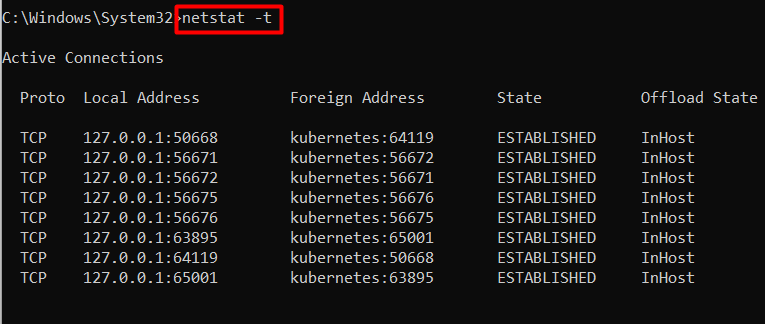
That’s all for the netstat command in Windows.
Final Words
The netstat command lets you view your network’s statistics. It includes several flags/options that output distinct information according to your requirements. This guide has explained the netstat command and its flags using the examples in detail.