This document shows you how to install and configure secure ProFTPD server on Ubuntu 14.10. ProFTPD is a free FTP server that allows you to upload/download and share content via FTP protocol.
FTP protocol is inherently insecure. Without encrypting the network traffic and packets between the FTP client and server, your data may be intercepted and view using the right tool. This brief document will show you how to install ProFTPD server as well as enable encryption to protect your data.
So, to get started, continue below.
- Installing ProFTPD server on Ubuntu 14.10
To install ProFTPD on Ubuntu 14.10, run the commands below
sudo apt-get install proftpd
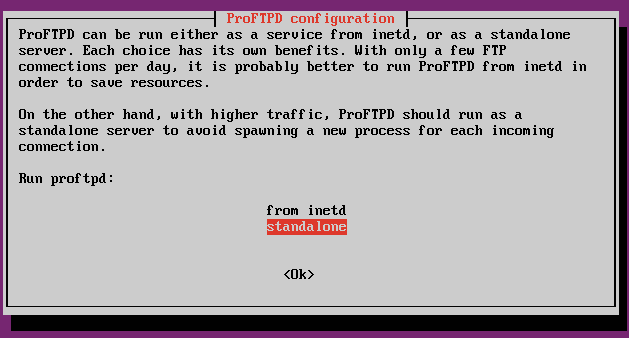
During the installation, you’ll be prompted to select the installation method of your choice. There are two installation methods; standard daemon and the inet daemon methods.
Each has it own benefits and risks. The standard daemon are for servers that are getting high FTP connections per day. If your site is only getting a few FTP connections per day, then it’s recommended to go with the inet daemon installation.
ProFTPD can be run either as a service from inetd, or as a standalone server. Each choice has its
own benefits. With only a few FTP connections per day, it is probably better to run ProFTPD from inetd in order to save resources.
On the other hand, with higher traffic, ProFTPD should run as a standalone server to avoid spawning a new process for each incoming connection.
Run proftpd:
After installing, run the commands below to check the version installed.
proftpd -v
The installation is simple and quick. To configure ProFTPD, do it in its default configuration file at /etc/proftpd/proftpd.conf.
After making changes to ProFTPD, run the commands below to restart the server
sudo service proftpd restart
At this stage, anyone with valid account on the system may use FTP services as long as the account isn’t banned or on the do-not-access-list. To access the server, open any modern web browser and type ftp://server_name or ftp://server_IP_Address.
- Securing ProFTPD server using SSL
ProFTPD is installed and configured, but it isn’t secure. Traffic to and from the server my be sent in clear text which can be viewed by anyone with the right tools. To encrypt all FTP traffic, continue below.
Type the commands below to open ProFTPD configuration file
sudo vi /etc/proftpd/proftpd.conf
Then uncomment the line below
[....]
# This is used for FTPS connections
Include /etc/proftpd/tls.conf
[....]
Save the file and close out.
Next, open ProFTPD tls.conf file by running the commands below
sudo vi /etc/proftpd/tls.conf
Then make the below changes in the file and save.
# Proftpd sample configuration for FTPS connections.
#
# Note that FTPS impose some limitations in NAT traversing.
# See http://www.castaglia.org/proftpd/doc/contrib/ProFTPD-mini-HOWTO-TLS.html
# for more information.
#<IfModule mod_tls.c>
TLSEngine on
TLSLog /var/log/proftpd/tls.log
TLSProtocol SSLv23
#
# Server SSL certificate. You can generate a self-signed certificate using
# a command like:
#
# openssl req -x509 -newkey rsa:1024 \
# -keyout /etc/ssl/private/proftpd.key -out /etc/ssl/certs/proftpd.crt \
# -nodes -days 365
#
# The proftpd.key file must be readable by root only. The other file can be
# readable by anyone.
#
# chmod 0600 /etc/ssl/private/proftpd.key
# chmod 0640 /etc/ssl/private/proftpd.key
#
TLSRSACertificateFile /etc/ssl/certs/proftpd.crt.pem
TLSRSACertificateKeyFile /etc/ssl/certs/proftpd.key.pem
#
# CA the server trusts…
#TLSCACertificateFile /etc/ssl/certs/CA.pem
# …or avoid CA cert and be verbose
#TLSOptions NoCertRequest EnableDiags
# … or the same with relaxed session use for some clients (e.g. FireFtp)
#TLSOptions NoCertRequest EnableDiags NoSessionReuseRequired
#
#
# Per default drop connection if client tries to start a renegotiate
# This is a fix for CVE-2009-3555 but could break some clients.
#
#TLSOptions AllowClientRenegotiations
#
# Authenticate clients that want to use FTP over TLS?
#
TLSVerifyClient off
#
# Are clients required to use FTP over TLS when talking to this server?
#
TLSRequired on
#
# Allow SSL/TLS renegotiations when the client requests them, but
# do not force the renegotations. Some clients do not support
# SSL/TLS renegotiations; when mod_tls forces a renegotiation, these
# clients will close the data connection, or there will be a timeout
# on an idle data connection.
#
#TLSRenegotiate required off
</IfModule>
Save the file.
Next, create a folder to store the server certificates keys.
sudo mkdir /etc/ssl/certs
Then run the commands below to generate encryption keys.
sudo openssl req -new -x509 -days 365 -nodes -out /etc/ssl/certs/proftpd.crt.pem -keyout /etc/ssl/certs/proftpd.key.pem
After the following prompts
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:Minnesota
Locality Name (eg, city) []:Minn
Organization Name (eg, company) [Internet Widgits Pty Ltd]:My Blog
Organizational Unit Name (eg, section) []:Dept of Blogging
Common Name (e.g. server FQDN or YOUR name) []:myblog.com
Email Address []:[email protected]
When you’re done, restart ProFTPD server.
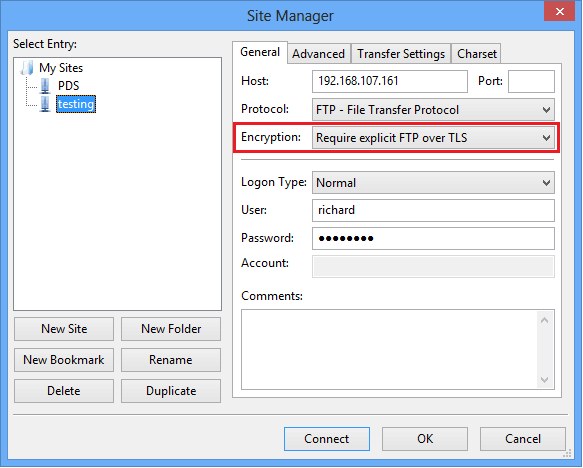
Next, go and open your FTP client and configure a TLS encryption profile
Then connect. When prompted and asked if you trust the key, click OK
That’s it!
Enjoy!