This brief tutorial is going to show you how to install and enable OpenSSH Server in Ubuntu 13.04 / 12.10 and older. I am also going to show you how to login via public key authentication without passwords.
The benefit of using SSH key to sign in is to protect yourself against brute-force password guessing attack. This attack consists of systematically checking all possible passwords until the correct one is found.
Since we’re going to disable password login for SSH, brute force attack will be completely unworkable in this setup.
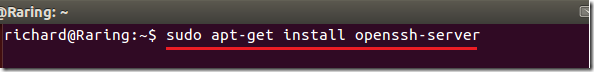
To get started, press Ctrl – Alt – T on your keyboard to open the terminal. When it opens, run the commands below to install OpenSSH Server in Ubuntu.
sudo apt-get install openssh-server
The server is installed and by default ready to accept connections via port 22. Now that SSH server is installed on the Ubuntu server, use the client machine to create a public / private key so that both systems will use. The client will keep the private key and the server will use the client’s public key to authenticate the client.
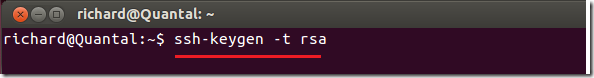
To generate the keys, run the commands below from the client machine. The client may be a Linux machine or another OS machine like Windows or Mac with command line option to export SSH keys. After running the commands, it will prompt you to create passphrase and passwords, for the keys, don’t enter any just press Enter to skip until the keys are generated.
ssh-keygen -t rsa
Next, create a hidden .ssh folder in your home directory on the server by running the commands below. If the folder is already created, then skip below.
mkdir -p ~/.ssh
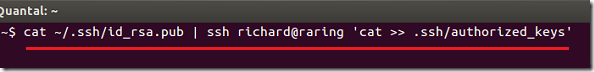
Next, run the commands below to export the client public key to the server’s ssh authorized_keys file.
cat ~/.ssh/id_rsa.pub | ssh richard@server_name 'cat >> .ssh/authorized_keys'
replace server_name with your server name.
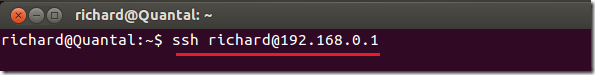
If everything goes as planned, you should be able to access the server without password by running the commands below.
ssh username@server_name
replace username & server_name with your own info
Now go and open ssh configuration file and make sure that only users with the private key will be allowed in. To do that, run the commands below.
sudo vi /etc/ssh/sshd_config
Than, change the line below to
PasswordAuthentication no
Restart SSH by running the commands below.
sudo /etc/init.d/ssh restart
If you run into trouble and see the error message ‘Agent admited failure to sign using the key’, run the command below on the client machine to enable managed ssh-agent.
ssh-add
Also, if you’re getting ‘Permission denied (publickey)’, open ssh configuration file and change the line to look like this.
ChallengeResponseAuthentication no
Public key login will only be permitted if these two lines are enable in ssh config file.
RSAAuthentication yes
PubkeyAuthentication yes
PermitRootLogin no
Enjoy!